Duties of Subscribers
Chapter VI of the ICT Act, 2006 requires rearrangement because of technology neutral concept. The matter relating to digital certificate is placed first , then duties of the subscribers in case of certificate other than digital certificate
Secs. 41-44 [ICT Act, 2006]
41. Application of security procedure.–The subscriber shall apply required security procedure to ensure the purity of Digital Signature Certificate issued by a Certifying Authority.
42. Generating Key Pair
Where any Digital Signature Certificate, the public key of which corresponds to the private key of that subscriber which is to be listed in the Digital Signature Certificate has been accepted by a subscriber the subscriber shall generate that key pair by applying the security procedure.
Security Guidelines for Certifying Authorities of Rule 20 of the IT (CA) Rules, 2010; Standards of Key Pair of Rule 7 of the IT (CA) Rules, 2010 and Application of security procedure of Sec. 41 of ICT Act, 2006.
Standards of Key Pair
- Standards – The Information Technology architecture followed by Certifying
Authorities shall be of appropriate and acceptable standards and the activities of such authority shall be in accordance with the standards as set out in Schedule-2 or as prescribed by the Controller from time to time.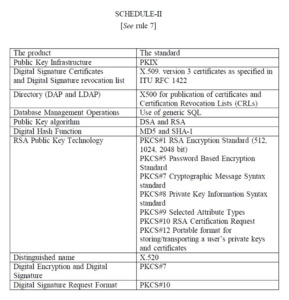
Rule 20 of the IT (CA) Rules, 2010-
- 20. Security Guidelines for Certifying Authorities– (1) The Certifying Authorities shall have the responsibility of integrity, confidentiality and protection of information and information assets employed in its operation, considering classification, declassification, labeling, storage, access and destruction of information assets according to their value, sensitivity and importance of operation.
(2) The controller shall issue the Information Technology Security Guidelines and Security Guidelines for Certifying Authorities aimed at protecting the integrity, confidentiality and availability of service of the Certifying Authority.
(3) The Certifying Authority shall formulate its Information Technology and Security Policy within 60 (sixty) days after issuance of the licence for operation complying with these guidelines and submit the same to the Controller before commencement of operation:
Provided that the controller may make any change(s) in the Information Technology and Security Policy formulated by the Certifying Authority if the Controller thinks fit and the Controller shall inform such amendment to the Certifying Authority within 4(fourteen) days from the date of its submission to the Controller.
Rule 21 of the IT (CA) Rules, 2010-
Dual Key Pair
- Commencement of Operation by Licensed Certifying Authorities– The licensed Certifying Authority shall commence its operation and issue of Digital Signature only after the following activities completed; namely –
(a) it has confirmed to the Controller the adoption of Certification Practice Statement; [CPS]
(b) it has generated its key pair, namely, private and corresponding public key, and submitted the public key to the Controller;
(c) the installed facilities and infrastructure associated with all functions of generation, issue and management of Electronic Signature Certificate have been audited by the accredited auditor in accordance with the provisions of rule 32; and
(d) it has submitted the arrangement for cross certification with other licensed Certifying Authorities to the Controller.
Secs. 41-44 [ICT Act, 2006]
- 42. Acceptance of Digital Signature Certificate.—
(1) A subscriber shall be deemed to have accepted a Digital Signature Certificate if he publishes or authorizes the publication of a Digital Signature Certificate to one or more persons or in a repository.
(2) By accepting Digital Signature Certificate the subscriber certifies to all who reasonably rely on the information contained in the Digital Signature Certificate that–
(a) all representations made by the subscriber to the Certifying Authority and all materials relevant to the information contained in the Digital Certificate are true; and
(b) all information in the Digital Signature Certificate that is within the knowledge of the subscriber is true.
Secs. 42 of ICT Act, 2006 and Rule 24 of the IT (CA) Rules, 2010-
Seb-section (1) of the section 42 of the ICT Act, 2006 Acceptance of Electronic Signature Certificate is directly related to its publication. It has been provided under the [rule 24(g) that the Certifying Authority shall provide a reasonable opportunity for the subscriber to verify the contents of the Electronic Signature Certificate before it is accepted; it is further provided that upon acceptance of the Electronic Signature Certificate, the Certifying Authority shall publish a signed copy of the Electronic Signature Certificate [rule 24(h);
Secs. 42 of ICT Act, 2006 andRule 25 of the IT (CA) Rules, 2010-
- Generation and usages of Electronic Signature Certificate –
The usages and transmission of the Electronic Signature Certificate shall involve the following, namely :-
(a) receipt of an approved and verified Electronic Signature Certificate request;
(b) creation of a new Electronic Signature Certificate;
(c) binding the key pair associated with the Electronic Signature Certificate to a Electronic Signature Certificate owner;
(d) a distinguished name associated with the Electronic Signature Certificate owner;
(e) a recognized and relevant name as defined in Certification Practice Statement.
Secs. 41-44 [ICT Act, 2006]
- 43. Presumption of represented information of obtaining Digital Signature Certificate.–
All material representations made by the subscriber to a Certifying Authority for purposes of obtaining a certificate, including all information known to the subscriber and represented in the Digital Signature Certificate, shall be accurate and complete to the best of the subscriber’s knowledge and belief, regardless of whether such representations are confirmed by the Certifying Authority.
- Control of safety measure of subscriber.–(1) Every subscriber shall exercise reasonable care to retain control of using of Digital Signature Certificate and take all steps to prevent its disclosure to a person not authorized to affix the digital signature of the subscriber.
(2) If the security of Digital Signature Certificate has been compromised by disobeying the rules in sub-section (1) of this section, the subscriber shall communicate the same without any delay to the Certifying Authority who has issued the Digital Signature Certificate in an agreed manner.
Sample Questions
- What do you mean by subscriber under ICT Act, 2006? (Answer: Bangladesher Cyber Ain: Totto o Bisleshon By Dr. Zulfiquar Ahmed, p. 92)
- Who is Subscriber?/Who is a subscriber in ICT Act, 2006? (Answer: Bangladesher Cyber Ain: Totto o Bisleshon By Dr. Zulfiquar Ahmed, p. 92)
- Who Can be a Subscriber? (Answer: Bangladesher Cyber Ain: Totto o Bisleshon By Dr. Zulfiquar Ahmed, pp. 92 & 565-566)
- What are the Duties of Subscribers? (Answer: Bangladesher Cyber Ain: Totto o Bisleshon By Dr. Zulfiquar Ahmed, pp. 287-290)
- What are the Steps to become a Subscriber? (Answer: Bangladesher Cyber Ain: Totto o Bisleshon By Dr. Zulfiquar Ahmed, pp. 92, 287-290 & 565-566)
